Threat Protection - Professional Services & Engineering
ThreatRadius365
CloudVertical’s ThreatRadius365 services offering enables your team to solidly advance adoption of Microsoft Defender & CASB pillars while extending protection to your SaaS app thru enablement of:
SaaS app discovery & posture management: Prevention is the key. It begins with discovery, which is crucial for understanding the applications being used in your environment.
SaaS threat protection: CloudVertical will help your team leverage advanced hunting capabilities across apps, identities, endpoints, and email to provide security teams with extensive SaaS threat protection.
Security for AI apps: We drive AI security capabilities that enable your SOC/NOC teams to gain full visibility into the AI applications used within your environment, as well as to detect and respond to suspicious interactions with GenAI apps like Copilot for Microsoft 365.
App-to-app protection: We provide app-to-app protection through app governance. This pillar specifically addresses OAuth apps, which can often serve as backdoors for adversaries. Just as we consider user interactions with apps, we apply similar principles to how apps interact with one another, focusing on both posture and threat protection.
Data protection: After connecting your apps using Microsoft’s API connectors, you will gain visibility into the files stored within those apps. It is important to classify, label, and implement policies to prevent data leakage.
ThreatRadius365 Value Proposition
Fortify - Automate - Accelerate
Fortify your ecosystem with Microsoft Defender. Our engineering team will expertly deploy and configure the implementation of the Microsoft Defender suite to enable automation and your team’s adoption of advanced protection. Accelerate incident response—across your entire ecosystem.
ThreatRadius365 Foundations
Foundation 1 - Defender for Endpoints
Centralized Security Operations: Defender for Endpoint provides a centralized security operations experience for Windows and non-Windows platforms. You'll be able to see alerts from various supported operating systems (OS) in Microsoft 365 Defender and better protect your organization's network.
Supported platforms include:
Endpoints and servers: Windows, MacOS, Linux
Mobile threat defense: Android, iOS
Virtual Desktops: Windows 365, Azure Virtual Desktop
Network devices:
Cisco IOS, IOS-XE, NX-OS
Juniper JUNOS
HPE ArubaOS, Procurve Switch Software
Palo Alto Networks PAN-OS
Endpoint Visibility and Continuous Discovery: 24x7x365 real-time discovery. Context-aware prioritization. Integrated and pre-built end-to-end remediation.
Automated & Proactive Threat Detection-Remediation: 1-click remediation via Intune/SCCM. Automated task monitoring via run-time analysis. Ticket management integration (Intune, Planner, ServiceNow, JIRA)
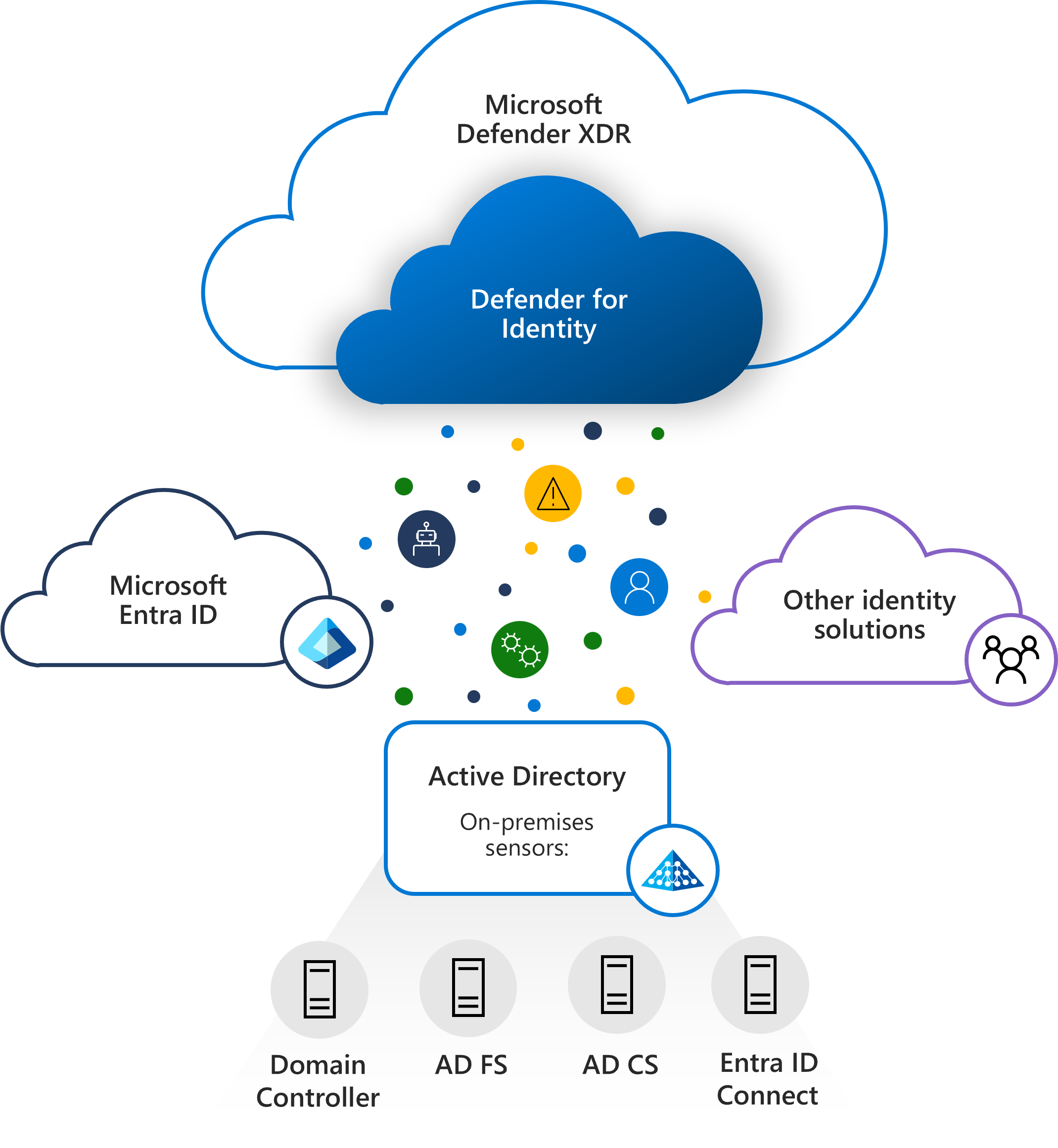
Foundation 2 - Defender for Identity
Prevent:
Defender for Identity offers agents and connectors for identities and infrastructure on-premises or in the cloud to deliver comprehensive coverage for your unique environment.
Gain visibility across your entire identity landscape with a consolidated view of identities within the context of your security operations center (SOC) experience.
Proactively assess your identity landscape and leverage best practices to stop common attack
patterns before they become a problem with identity security posture assessments.
Detect:
Leverage out-of-the-box detections built from our expertise analyzing more than 72 trillion signals.
Pairing identity-specific alerts and detections with telemetry from
across the SOC to quickly spot advanced threats.Proactively hunt threats with an advanced hunting experience infused
with Security Copilot guidance and data from across security domains
Respond:
Automatic attack disruption -XDR-level intelligence and AI automatically disrupt advanced attacks before they can do more damage.
Copilot for Security Intelligence - AI guided experiences allow SOC
professionals to investigate security alerts and incidents in natural language.Improved ITDR efficiency - Eliminate potential gaps in identity threat detection with native integration and consistent alerts across SOC and identity teams
Foundation 3 - Defender for Cloud Apps
CloudVertical can help your team deploy and configure Microsoft Defender for CloudApps and extend protection in the following ways:
SaaS app discovery & posture management: Prevention is the key. It begins with discovery, which is crucial for understanding the applications being used in your environment. Sanctioning and unsanctioning apps help to identify which applications are approved for corporate use. The sanctioned apps, which include both those using app connectors and those identified through discovery, form the core of our protection strategy. Another essential component of prevention is SaaS security posture management (SSPM), which identifies misconfigurations in apps and provides recommendations for administrators to strengthen security posture. A stronger app posture reduces susceptibility to attacks.
SaaS threat protection: Modern attacks often span multiple domains, and SaaS-related threats are no different. Defender for Cloud Apps is natively integrated with Microsoft Defender XDR, leveraging advanced hunting capabilities across apps, identities, endpoints, and email to provide security teams with extensive SaaS threat protection.
Security for AI apps: With the rapid adoption of generative AI, it is critical for organizations to have the right tools to prevent and protect against AI-related threats. Defender for Cloud Apps offers capabilities that enable security teams to gain full visibility into the AI applications used within their environment, as well as to detect and respond to suspicious interactions with GenAI apps like Copilot for Microsoft 365.
App-to-app protection: We provide app-to-app protection through app governance. This pillar specifically addresses OAuth apps, which can often serve as backdoors for adversaries. Just as we consider user interactions with apps, we apply similar principles to how apps interact with one another, focusing on both posture and threat protection.
Data protection: After connecting your apps using our API connectors, you will gain visibility into the files stored within those apps. It is important to classify, label, and implement policies to prevent data leakage.
CloudVertical Defender Capabilities Overview
Need A Demo or Assistance Evaluating Defender?